Use VCE Exam Simulator to open VCE files

This Chapter covers following Topic Lessons
This Chapter covers following Lab Exercises
In this chapter we will add Azure Storage Account to the topology. We will create two Storage Accounts - GPv2 Standard Storage Account & GPv2 Premium Storage Account.
An Azure storage account provides a unique namespace to store and access your Azure Storage data objects.
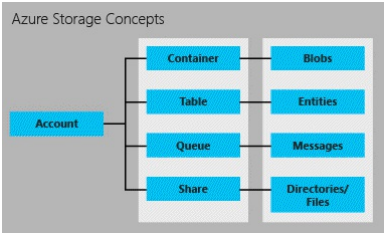
Azure Storage (Blob, Table, Queue and Files) is created under Storage Accounts. Storage Account is prerequisite for creating Azure Storage.
The image below shows the dashboard of General Purpose Storage Account. From here you will create Blob, File, table or Queue Storage.
Figure below shows components of Blob, Table, Queue and File Storage.
There are three types of storage accounts - General-purpose v2 (GPv2) Storage Account, General-purpose v1 (GPv1) Storage Account & Blob Storage Account.
General-purpose v2 (GPv2) storage accounts support storage services including blobs, files, queues, and tables. It supports all latest features for storage services.
For block blobs in a GPv2 storage account, you can choose between hot and cool storage tiers at the account level, or hot, cool, and archive tiers at the blob level.
General-purpose v1 (GPv1) storage account supports storage services including blobs, files, queues, and tables. It does not support latest features for storage services. It does not support blob storage tiering.
Blob Storage accounts are specialized for storing blob data and support choosing an access tier - Hot or cool at account level. Blob storage accounts support only block and append blobs and not page blobs.
A standard storage performance tier allows you to create Blobs, Tables, Queues, Files and Azure virtual machine disks.
It is backed by magnetic disk HDD.
Supports GPv1, GPv2 and Blob Storage Account.
A premium storage performance tier allows you to create Blobs and Azure virtual machine disks.
It is backed by SSD.
Supports GPv1 & GPv2 Storage Account. Supports LRS replication only
Note: Premier storage performance tier now also supports and Azure File Storage (Preview). It is in Preview as of writing.
Note: MS now recommends Managed disks for Azure VMs. Managed Disks obviates the need to have storage account. Managed disks only support LRS for replication.
The data in the Microsoft Azure storage account is always replicated to ensure high availability. Replication copies data, either within the same Data Centre, or to a second Data Centre, depending on the replication option chosen. Azure Storage Accounts offer 4 Replication options - LRS, ZRS, GRS, RA-GRS.
Locally redundant storage (LRS) replicates your data three times in a datacenter in the region in which you created your storage account. A write request returns successfully only once it has been written to all three replicas. The three replicas each reside in separate fault domains and upgrade domains within one storage scale unit.
LRS is the lowest cost option. LRS can protect your data from underlying storage node failure but not from Data Centre wide outage.
LRS can be used in cases where applications are restricted to replicating data only within a country due to data governance requirements.
Storage Accounts Supported: GPv2, GPv1 and Blob Storage Account.
ZRS replicates your data synchronously across three availability zones. ZRS enables customers to read and write data even if a single zone is unavailable or unrecoverable. Inserts and updates to data are made synchronously and are strongly consistent.
ZRS provides durability for storage objects of at least 99.9999999999% (12 9's) over a given year. Consider ZRS for scenarios like transactional applications where downtime is not acceptable.
ZRS provides higher durability than LRS. Data stored in ZRS is durable even if the primary Datacentre is unavailable or unrecoverable.
ZRS will not protect your data against a regional disaster where multiple zones are permanently affected. For protection against regional disasters, Microsoft recommends using Geo-redundant storage (GRS): Cross-regional replication for Azure Storage.
Storage Accounts Supported: GPv2.
Geo-redundant storage (GRS) replicates your data to a secondary region that is hundreds of miles away from the primary region.
With GRS, data is first replicated 3 times within the primary region and then asynchronously replicated to the secondary region, where it is also replicated three times.
With GRS, data is durable even in the case of a complete regional outage or a disaster in which the primary region is not recoverable.
When you create a storage account, you select the primary region for the account. The secondary region is determined based on the primary region, and cannot be changed.
Storage Accounts Supporte d: GPv2, GPv1 and Blob Storage Account.
Read-access geo-redundant storage (RA-GRS) not only replicates your data to a secondary region but also provides read-only access to the data in the secondary location.
With RA-GRS, data is first replicated 3 times within the primary region and then asynchronously replicated to the secondary region, where it is also replicated three times.
With RA-GRS, data is durable even in the case of a complete regional outage or a disaster in which the primary region is not recoverable.
When you create a storage account, you select the primary region for the account. The secondary region is determined based on the primary region, and cannot be changed.
Storage Accounts Supported : GPv2, GPv1 and Blob Storage Account.
Every object that you store in Azure Storage has a unique URL address. The storage account name forms the subdomain of that address. The combination of subdomain and domain name, which is specific to each service, forms an endpoint for your storage account.
For example, if your storage account is named mystorageaccount, then the default endpoints for your storage account are:
Blob service: http://mystorageaccount.blob.core.windows.net
Table service: http://mystorageaccount.table.core.windows.net
Queue service: http://mystorageaccount.queue.core.windows.net
File service: http://mystorageaccount.file.core.windows.net
The URL for accessing an object in a storage account is built by appending
the object's location in the storage account to the endpoint. For example, a
blob address might have this format:
http://mystorageaccount.blob.core.windows.net/mycontainer/myblob.
You can also configure a custom domain name to use with your storage account.
In this exercise we will create Standard GPv2 Storage Account with name sastdcloud in resource group RGCloud and in location US East 2.
In Azure Portal Click +Create a Resource in left pane>Storage> Storage Accounts> Create Storage Account Blade opens> Select Resource Group RGCloud > Give a unique name to storage Account sa stdCloud > Select location East US 2>Performance standard>Account Type as GPv2>Replication RA-GRS> Access Tier Hot> Rest keep as default> Click Next: Advanced
Note 1: Storage Account name has to be unique within Azure.
Note 2: You can choose between Standard or premium (SSD) performance
Tier.
Note 3: Note Access Tier option. This is not available with GPv1 Account.
In Advanced screen just go through options. Keep everything at default and click Review +create.
After validation is passed click create (Not Shown).
Figure below shows the dashboard of Storage Account. From here you can create Blob, file, table or queue Storage.
In this exercise we will create Premium GPv2 Storage Account with name sapremcloud in resource group RGCloud and in location US East 2.
In Azure Portal Click Storage Accounts in left pane> Storage Accounts Dashboard opens> Click + Add> Create Storage Account Blade opens> Select Resource Group RGCloud > Give a unique name to storage Account sapremcloud > Select location East US 2>Performance Premium>Account Type as GPv2>Replication LRS> Rest keep as default> Click Review +create>After Validation is passed click create
Note: Read the explanation under Replication.
Figure below shows the dashboard of Storage Account sapremcloud.
With Premium Account only Page Blob Storage option is there. This only supports Page Blobs. Recall that Page Blobs are used for Virtual Machine Disks.
Note: Premier storage performance tier now also supports and Azure File Storage (Preview). It is in Preview as of writing.
Figure below shows dashboard of GPv2 Storage Account sastdpcloud . From here you can create Blob, file, table or queue Storage.
Change configuration of storage account: Click configuration in left pane. From here you can change Access tier and Replication option.
Storage Account Security with RBAC: By default owner can access the Storage Account. You can delegate the Storage Account administration using Role Based Access control (RBAC). You can assign role of an owner, contributor, reader, Backup operator etc depending upon your requirement.
Note: RBAC will be extensively discussed in Chapter 16.
Go to sastdcloud Dashboard>Click Access Control (IAM) in left pane>+ Add Role assignment>Add role assignment blade opens> Select the role and the user.
Storage Account Security with Storage Service Encryption (SSE): By default SSE protects your data at Rest using MS managed keys. You can use your own to keys to encryption storage data.
Click encryption in left pane> check box use your own key and select Key vault and key.
Storage Account Security using Azure Virtual Network Service Endpoints : By default owner can access storage account from internet. This is a security loophole. Using Firewall and Virtual Network option you can limit access to Storage account from Virtual Network only. You also have the option of allowing Storage account access from internet from particular IP address only.
Click Firewall and Virtual Networks in left pane>Click Add existing Virtual Network>Select your Virtual Network.
In Next section we will discuss in detail about Azure Virtual Network Service Endpoints.
Azure Managed Resources such as Azure Storage or Azure SQL Database can be accessed from outside Azure and by VMs in Virtual Network over internet connection.
With Azure Virtual Network Service Endpoints, traffic between Azure Virtual Network and Azure Managed Resources such as Storage Accounts remains on the Microsoft Azure backbone network and not on Public Internet.
Figure below shows the Architecture of VNET Service Endpoints. Resources in Virtual Network are accessing Azure Storage over Microsoft backbone network.
Azures Managed Resources such as Azure Storage and Azure SQL have Internet facing IP addresses. Because of security reasons many customers prefer that their Azure Managed Services not be exposed directly to the Internet.
Virtual Network Service Endpoints are created in Virtual Network and are attached to Subnets. They extend Azure Virtual Network private address space to Azure Managed services. You can also restrict Azure resources to only be accessed from your VNET and not via the Internet. You also have the option to allow access from internet or from particular IP range only.
In this Exercise we will create VNET Service Endpoints for Azure Storage Account sastdcloud. After setting up Service Endpoint and blocking access of Azure Storage Account from internet we will check whether we can still open HelloWorld.txt @ https://sastdcloud.blob.core.windows.net/hk410/HelloWorld.txt We will then access HelloWorld.txt using Internet Explorer from Azure VM VMF1 located in Web-Subnet in Virtual Network VNETCloud.
Note for the Readers: Attempt this exercise after you have completed Exercise 64, Chapter 6. In Storage chapter 6 we created Container hk410 and uploaded HelloWorld.txt with Anonymous access.
Step 1: Check whether you can access Hello World.txt from internet or not @ https://sastdcloud.blob.core.windows.net/hk410/HelloWorld.txt HelloWorld opens from Internet.
Step 2: Go the Virtual Network VNETCloud Dashboard> click Service endpoints in left pane> Click +Add> Add service endpoints blade opens> Select Storage from Service Dropdown box and Web-subnet from Subnets dropdown box>click Add (Not Shown).
Note: Readers are requested to See service Endpoint options in service dropdown box.
Step 3: Go Storage Account sastdcloud dashboard>Click Firewalls and Virtual Networks in left pane>Click selected Networks Radio Button in right pane>click +Add Existing Virtual Network> Add Network blade opens>Select VNETCloud from Virtual Networks Dropdown box and WebSubnet from Subnets dropdown box and click Add>click save.
Note Firewall option: Here you can add IP address range which can access Azure storage from internet.
Step 4: Use Firefox to Check whether you can access Hello World.txt from internet or not @ https://sastdcloud.blob.core.windows.net/hk410/HelloWorld.txt The figure below shows that we cannot access HelloWorld.txt.
Step 4: Use Firefox to Check whether you can access Hello World.txt from internet or not @ https://sastdcloud.blob.core.windows.net/hk410/HelloWorld.txt The figure below shows that we cannot access HelloWorld.txt.
Step 5: RDP to Virtual Machine VMFE1>open internet explorer and log on Azure Portal @ https://portal.azure.com>Go to Storage Account sastdcloud Dashboard>In right pane Click Blobs>Click container hk410>Click Hello World.txt>Click download button at top>You get the option to open or save.
From above we infer that we cannot access HelloWorld.txt from internet but we can access from VM VMFE1 located in Web-Subnet using VNET Service Endpoints.
Note: Disable Internet Explorer Enhanced Security Configuration in Windows Server 2019 VM.
Step 6: Enable back Storage Account access from all Networks
In Storage Network sastdcloud Dashboard click Firewall and Virtual Networks in left pane>Select the radio button All Networks>Click save.
Note: We need access to Storage Account from internet for other exercises.
Microsoft Azure Storage Explorer is a standalone app (available on Windows, Mac & Linux) that allows you to easily work with Azure Storage data.
Using Storage Explorer you can Upload, download and manage blobs, files, queues, tables and Cosmos DB entities. Storage Explorer also provides easy access to manage your virtual machine disks.
Figure below shows Dashboard of Storage Explorer Application running on Windows Desktop.
Azure Account Subscription credentials
Storage Account Name and Key
Use a Shared Access Signature URI
Use a Connection String
By using Azure Subscription Account credentials with Azure Storage Explorer you get full access to all Storage Accounts in Azure Subscription.
Open Storage Explorer app on your desktop>In left pane right click Storage Accounts and click connect to Azure Storage> A dialog Box will pop and will show 5 options to connect to Azure Storage.
Select Add an Azure Account radio Button and click sign in box at the bottom of the Pop up dialog box>Sign-in to your account Blade will pop up. Enter your account credentials>click apply in Storage Explorer Dashboard. You can see all your storage Accounts (Created in Ex 54 & 55) in your subscription.
Enlarge the Storage Accounts and you can see the options available under each Storage Account. Storage Account sapremcloud has only Blob Storage option as it is was created with Premium Performance Tier (SSD) whereas Storage Account sastdportal has Blob, File, table and Queue option as it was created with Standard Storage Performance tier (HDD).
Note: Readers are advised to go through all the options here. Just Right click Blob Container and you can create a container. In next chapter we will show how to create a container and upload a file using Storage Explorer.
Using Azure Storage Explorer with Storage Account Access keys you get full access to that particular Storage Account only.
Anybody having access to Storage account key will have unlimited access to storage account.
Be careful not give account key to anybody as this will give them full access control to Storage Account.
In Azure Portal go to Storage Account sastdcloud dashboard>Click Access Keys in left pane> Copy Key 1 and paste in Notepad. We will use this to connect to storage Account using Storage Explorer.
In Storage Explorer Dashboard right click Storage Accounts and click connect to Azure Storage> A dialog Box will pop and will show 5 options to connect to Azure Storage>Select use a Storage account name and key radio button.
Select use a Storage account name and key radio button and click next button at bottom of the dialog box>Connect with Name and Key dialog box will pop up>Give a display name, enter Storage Account name sastdcloud in Account name and paste the key you copied previous exercise and click next.
Connection summary box will pop up>Click connect.
In Explorer Dashboard you can see SAKey. This name was given for storage Account sastdcloud in step 2. Expand Test-sastd and it will show all the 4 options-Blob, File, Queues and tables.
Anybody having access to Storage account key will have unlimited access to storage account.
Shared access signature (SAS), provide delegated access to a resource in your storage account, without having to share your account access keys. SAS is a secure way to share your storage resources without compromising your account keys.
A shared access signature is a token that encapsulates all of the information needed to authorize a request to Azure Storage on the URL. You can specify the storage resource, the permissions granted, and the interval over which the permissions are valid as part of the shared access signature.
You can provide a shared access signature to clients who should not be trusted with your storage account key but whom you wish to delegate access to certain storage account resources. By distributing a shared access signature URI to these clients, you grant them access to a resource for a specified period of time.
Service SAS delegates access to particular storage services: the Blob, Queue, Table, or File service.
An Account-level SAS can delegate access to multiple storage services (i.e. blob, file, queue, table).
n this exercise we will generate Shared Access Signature (SAS) for Storage Account sastdcloud for Blob service only.
In Azure Portal go to Storage Account sastdcloud dashboard>Click Shared Access Signature in left pane>In right pane under allowed service Select Blob only and rest select all default values>Click generate SAS and Connection String Box.
SAS will be generated and will be shown in bottom of the screen. Copy the Blob Service SAS URL.
In Storage Explorer Dashboard right click Storage Accounts and click connect to Azure Storage> A dialog Box will pop and will show 5 options to connect to Azure Storage>Select use a Shared Access Signature URI radio button.
Select use a shared access signature URL and Click next> Attach with SAS URI Blade opens>Enter a Display name >Enter URL which was generated in previous exercise and click Next>In summary box click connect.
In Storage Explorer dashboard you can see sasa-blob under Storage Account. We only have access to Blob Service as we have generated SAS for Blob service in previous exercise.
Inference from Previous Exercises
Accessing Azure Storage Accounts using Azure Account Credentials shows all the Storage Accounts created in the Subscription as we used Azure Subscription credentials for Connection.
Accessing Azure Storage Account using Storage Account Access Keys shows only one Storage Account sastdcloud with all four services (Blob, File, Queue and Table) listed. This connection used the Storage Account sastdcloud Access key.
Accessing Storage Account using Shared Access Signature showed only one Storage Account sastdcloud with Blob service listed. Shared access signature was generated for Storage Account sastdcloud blob service only. Similarly you can connect your application to Azure Storage by adding Shared Access Signature (SAS) or Storage Account key in your application code.
You can use Azure Active Directory (Azure AD) credentials to authenticate a user, group, or other identity for access to blob and queue data (preview). If authentication of an identity is successful, then Azure AD returns a token to use in authorizing the request to Azure Blob storage or Queue storage.
Note : Currently this feature is in preview and is not part of the exam and is not being discussed further.

Top Training Courses











LIMITED OFFER: GET 30% Discount
This is ONE TIME OFFER

A confirmation link will be sent to this email address to verify your login. *We value your privacy. We will not rent or sell your email address.
Download Free Demo of VCE Exam Simulator
Experience Avanset VCE Exam Simulator for yourself.
Simply submit your e-mail address below to get started with our interactive software demo of your free trial.