- Home
- Uncategorized
Uncategorized
6 Golden Rules to Follow: Ace Your Certification Exam with Ease!
There are many different tips and tricks that can help any individual prepare for various certification exams. These hints or lifehacks will significantly increase one’s chance of success. If you are new to the tests, it is essential to mention that they are quite different from your college and high school exams. The IT credentials are designed to evaluate specific skills that the professionals required to function optimally at their job roles. For example, apart from theoretical aspects, the certification tests also evaluate hands-on elements in many IT certificates. You…

7 Common Network Issues: Comprehensive Guide on How to Deal with Them
Things don’t always go the way we want. Despite all the best efforts to keep your networks running smoothly, things still happen, and you find yourself staring at the issues and wondering how you got there in the first place. You don’t need to panic when networks go awry. There are always things you can do to get everything back to shape. In this blog article, we will share with you some common network problems you are likely to come across and how you can quickly resolve them. We will…

How to Check and Configure Plugins in 5 Main Browsers?
The issues of cybersecurity continue to garner attention from different spheres of life. Many organizations have suffered major crises as a result of cyberattacks on their systems. The criminals go to any length to infect computers and steal data from unsuspecting victims. With the improvement in OS, it’s becoming very difficult for these cybercriminals to attack the lower layers. Since this option is almost impossible to penetrate for them, they have begun to explore other options to attack. Nowadays, they even carry out this hideous crime through browser plugins. It…
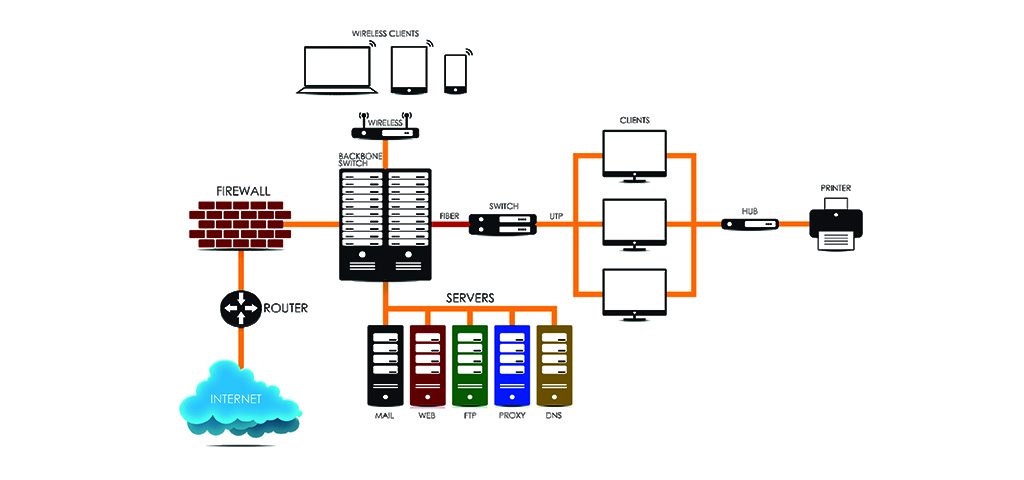
The CCAr, Cisco Certified Architect, credential commands a high level of respect. As a matter of fact, there is no other certificate that has the same reverence. It is one of those professional certifications that many people want to attain. The good news is that CCAr is attainable. Practically anyone can become a network design guru. It only requires serious hard work and the right quality of experience. Although this credential is totally achievable, the question that should be asked is whether it is really worth all the efforts. Prior…
Dive into the World of Microsoft MCSE Certifications!
The Microsoft certifications technically validate the knowledge, skills, and capabilities that the IT professionals need to carry out as well as prepare them to use the latest technologies. The certificates of this well-known vendor are some of the most sought-after ones in the IT industry. If you are planning to earn the Microsoft Certified Solutions Expert (MCSE) certificate, this guide is designed to provide you with comprehensive details about this certification track, how to prepare for the exams, and also what career and salary potential will await you. First, let’s…

Cloud Wars 2019: AWS vs Azure vs Google
The world of Cloud is dominated by three providers: Amazon, Microsoft, and Google. There is a consistent war for leadership and dominance going on between these three companies. No doubt, the clear leader among these three is Amazon, closely followed by Microsoft with Google coming behind. The reason for the war is very clear: the technological world has moved from the consideration of leveraging Cloud technology. It is now more of choices to make among the available providers. To tell the truth, each of the Cloud providers has its own…

5 Useful Tips: How to Conquer IT Job Search in This Digital Age?
The field of IT in the United States absorbs more than seven million professionals from the labor market. In comparison to many other industries, this figure is quite huge. As a matter of fact, the growth of IT is so rapid that there are over 600,000 jobs that are yet to be filled in the Information Technology realm. The increase in demand for the IT specialists has also directly affected the salary potential as it grows because of it. Based on the report, the average salary of an IT professional…

5 Easiest Jobs to Make a Successful IT Career
For the professionals in the world of IT, there are many opportunities out there to explore. In fact, there are times you have to make a decision between multiple offers of employment. With this, you can negotiate for better incentives and higher remuneration. This doesn’t mean that the story is the same for everyone trying to obtain employment in the industry. There are many people who have worked at the same job for years and seem to have been unable to get a more lucrative one. And there are other…

Main Certification Paths Every System Administrator Should Pursue
The system administrators are regarded as 360-degree professionals. Their job roles may include operational knowledge of almost all operating systems, ranging from IOS to Windows and Linux. No doubt, if you are a newbie in the IT industry, the prerequisite for taking up a job title as a system admin can be daunting. The learning process is tedious and requires high cerebral capacity but you can attain it if you put your mind to it. It may take time to get familiar with all the technologies, but you will definitely…
Top 5 Linux Certifications: Choose Your Best One!
Earning an IT certification is the way to go if you are planning on growing your career. For the tech professionals, the Linux credentials considered some of the best in the IT industry. That is why, in this blog article, we will take a look at the top five certificates that you might want to obtain before the end of this year. If earning such a credential is one of your goals for the nearest future, it is not late to pursue it. Let’s explore the best IT credentials that…



